Experience the Power of Productivity
Make your team 40% more efficient. Set up your account in just 2 minutes!

Limited insights into user behavior and activity patterns make it difficult to identify fraudulent activities.

The risk of insider threats might go unnoticed due to inadequate monitoring of employee activities and access patterns.

Inconsistent data protection fails to ensure comprehensive safeguarding, resulting in vulnerabilities and compromised data security.
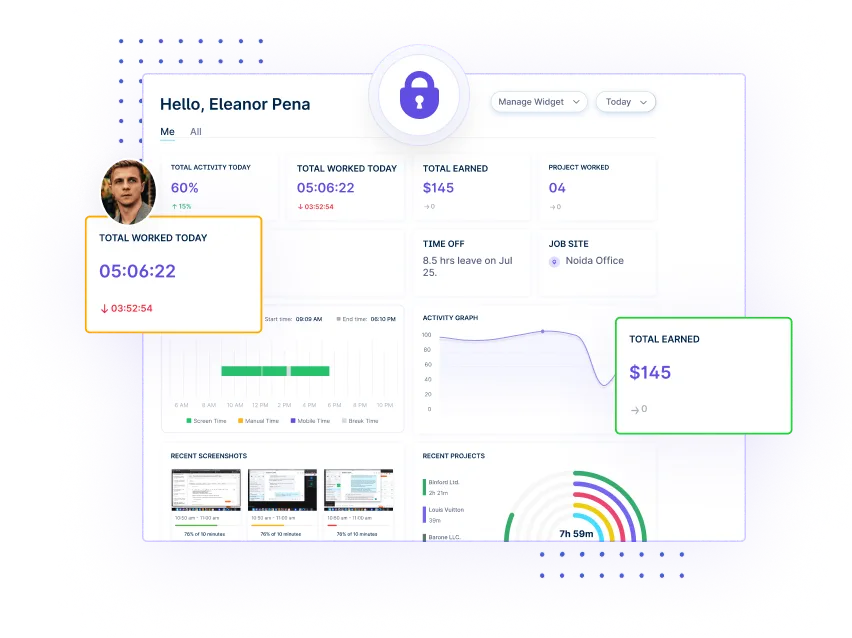
Monitor user activities continuously to spot potential fraud early. Take proactive measures to prevent fraudulent actions before they cause significant harm to your business.
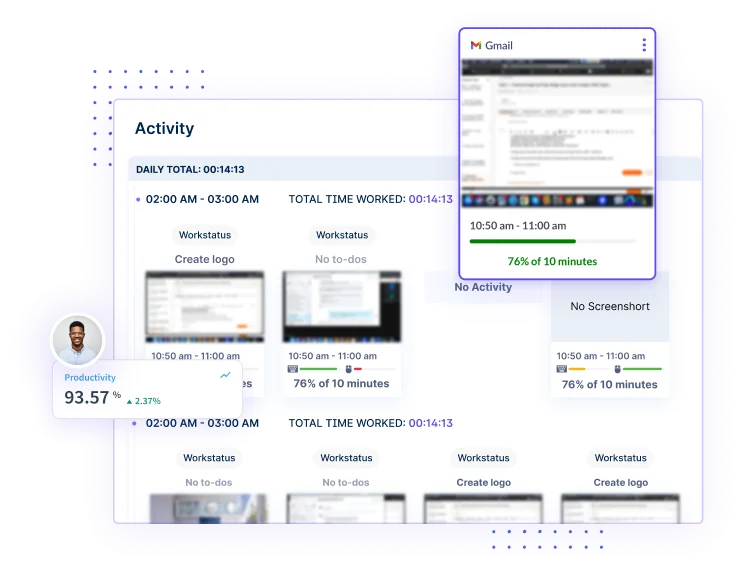
Get a visual record of what the user is doing, aiding in productivity monitoring, task verification, and ensuring accountability.

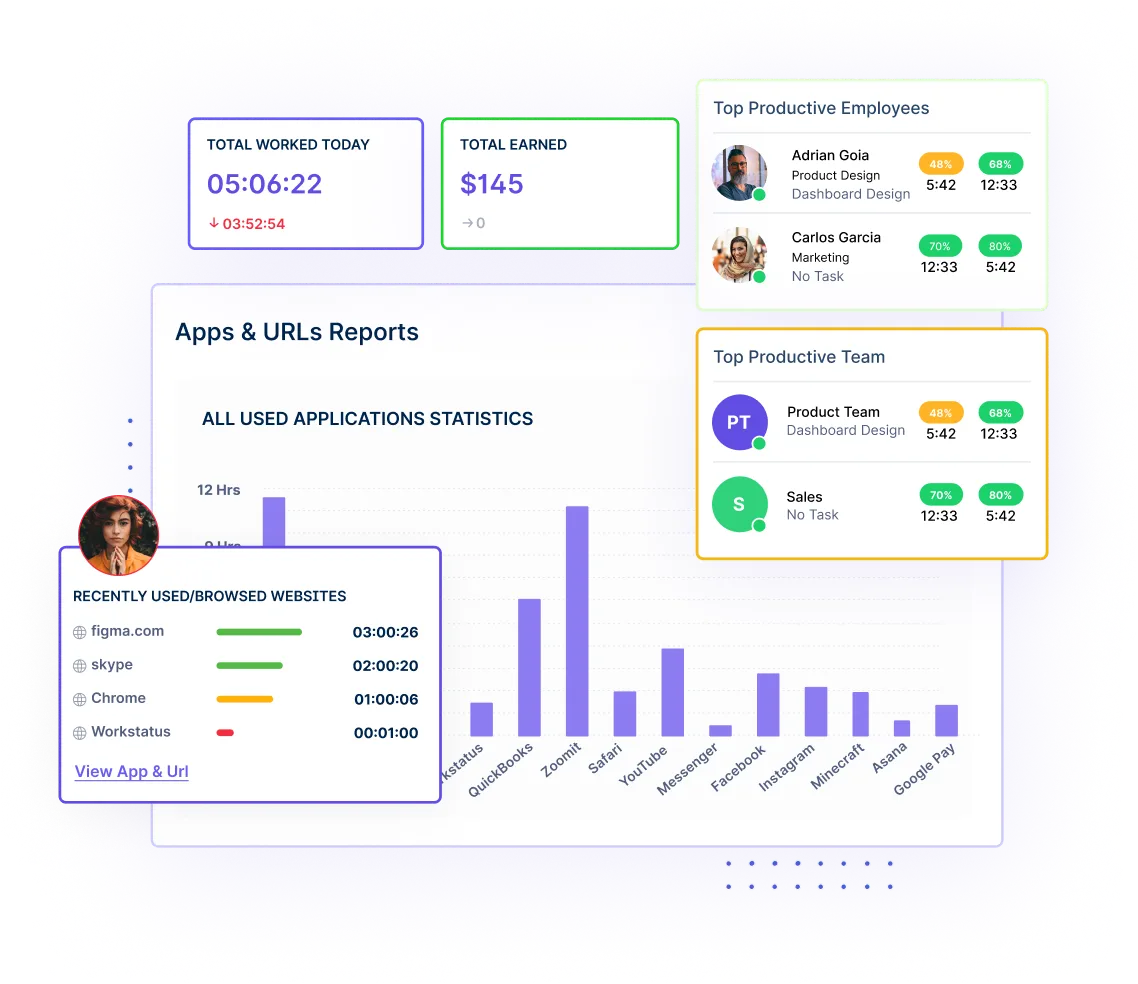
Analyze user behavior by tracking and logging the time spent on different apps and sites. It helps you spot deviations that signal potential fraud.

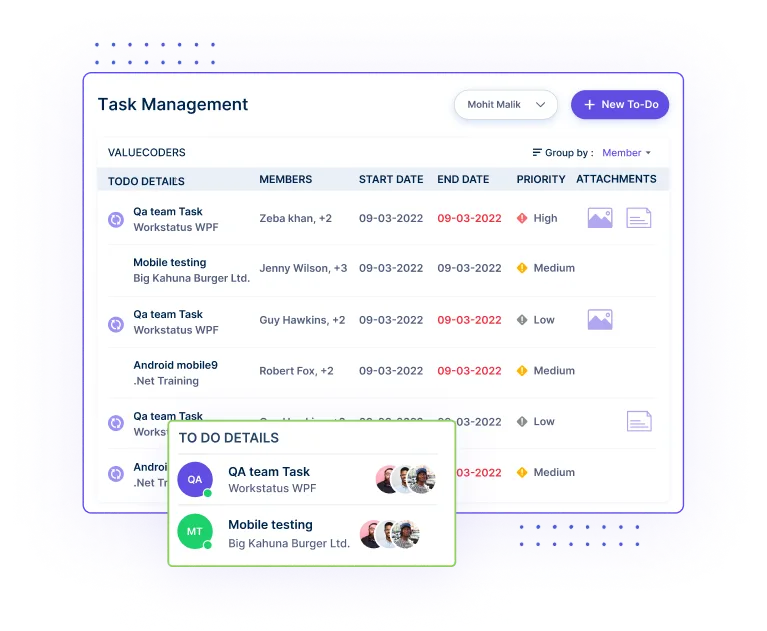
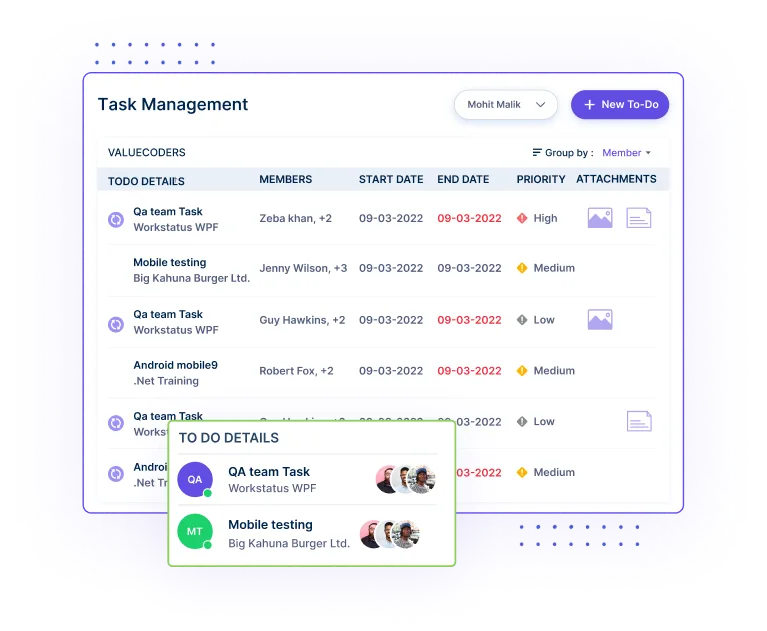
Control who has access to sensitive information and systems by setting permissions and regularly reviewing access rights.

Identify and mitigate insider threats to safeguard your company's sensitive data. Implement robust monitoring and security measures to prevent internal fraud.

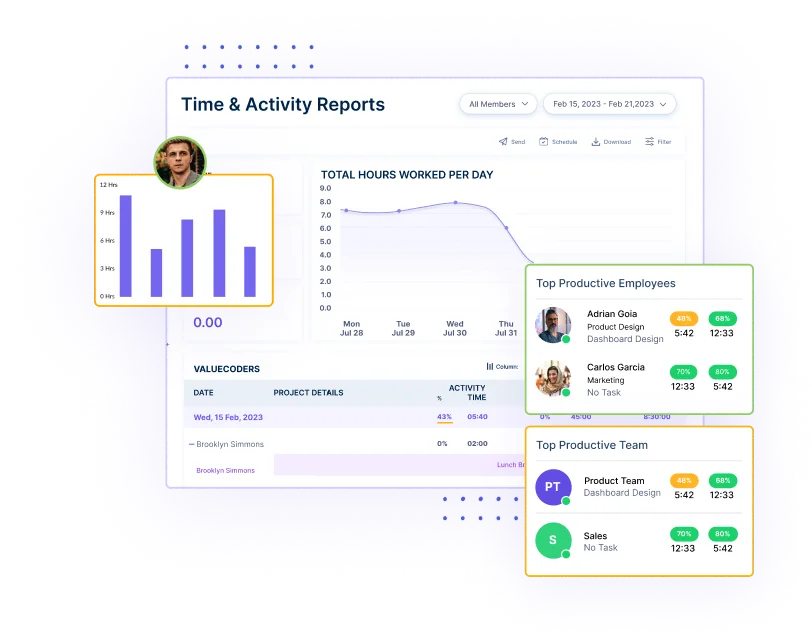
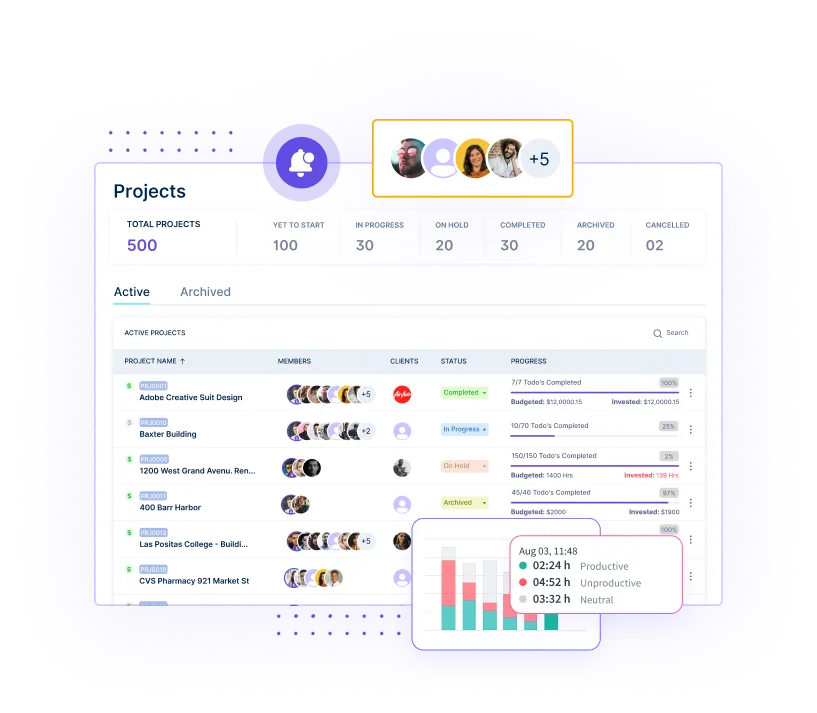
Analyze user activity to spot unusual or unexpected patterns that could indicate potential threats, enabling you to address issues before they escalate.

Review and update access permissions periodically to ensure they align with current roles and responsibilities.

Quickly respond to suspicious activity or unusual behavior to mitigate potential threats and prevent damage.

Protect your valuable information with robust security measures. Ensure your data is encrypted, securely stored, and regularly audited to prevent unauthorized access and breaches.
Workstatus complies with data security protocols, including SOC 2 Type II, PCI-DSS, ISO 22301, and ISO 27001 to ensure robust protection of sensitive information and resilience against security threats.

Get secure storage to protect sensitive data from unauthorized access and potential breaches, ensuring compliance and maintaining customer trust.

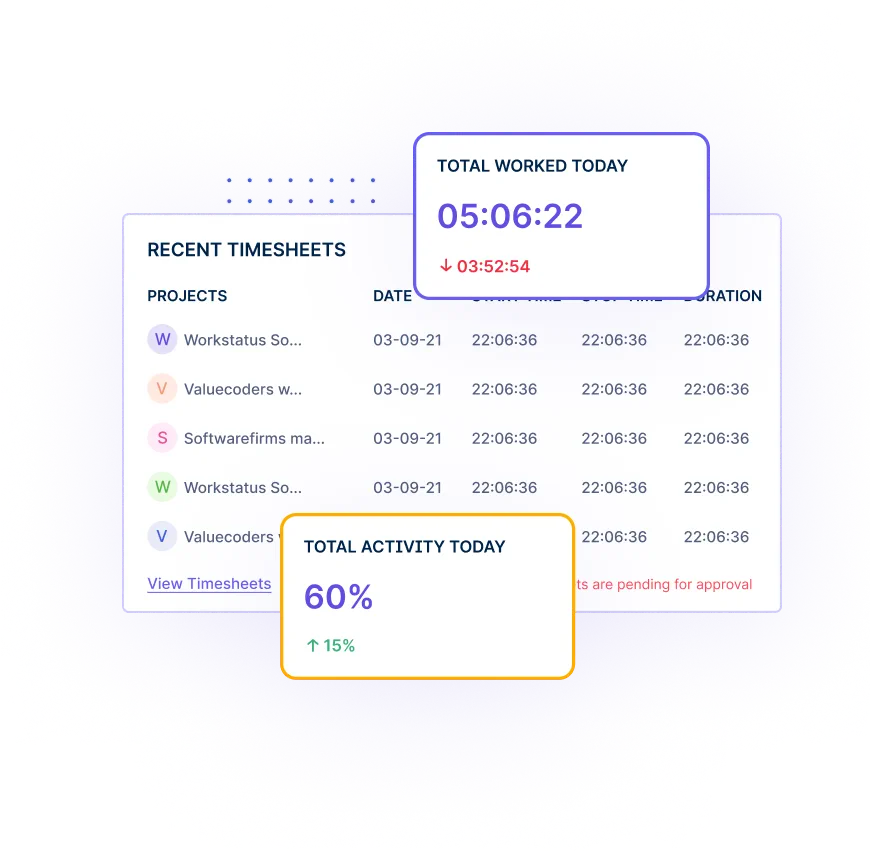
Workstatus simplifies auditing by providing detailed reports on time, activity, and attendance. This helps you verify data accuracy and integrity.

Our lightweight app allows you and your team to track time, no matter where you are. With GPS tracking and geofencing, anyone can clock in automatically when they enter a job site or get reminders based on location.
Workstatus account required to use apps
Yes, Workstatus enables monitoring across multiple devices, providing comprehensive insights into user behavior and interactions, regardless of the device used. This ensures a holistic view for detecting potential fraudulent activities.
Workstatus prioritizes data security. It encrypts user activity logs, implements stringent access controls, and follows industry-standard security protocols to safeguard sensitive information, ensuring confidentiality and integrity of monitored data.
The app & website monitoring tool in Workstatus tracks user activities by logging the time spent on various applications and websites during work hours, providing insights into productivity patterns.
Active screenshots are captured periodically by Workstatus at customizable intervals, such as every 5 minutes, 10 minutes,etc., providing a real-time visual record of user activities.
Track time and productivity effortlessly.
Customized Solutions for Maximum Productivity