Time & Attendance
Keep track of employee work hours and attendance with precision and ease.
Explore
Monitor real-time data interactions, detecting potential threats and maintaining the integrity of your valuable information. Leverage insights to fortify your data defense strategy.

Capture a detailed view of employees’ data-related activities, including accessed URLs, applications, and time allocations. Download comprehensive reports for thorough analysis and future reference.

Capture snapshots of employees’ active screens, providing evidence to support data-related billable hours without disrupting their workflow.
Entrust your data to Workstatus, the ultimate guardian. Experience unparalleled protection through real-time monitoring and swift responses to potential risks.

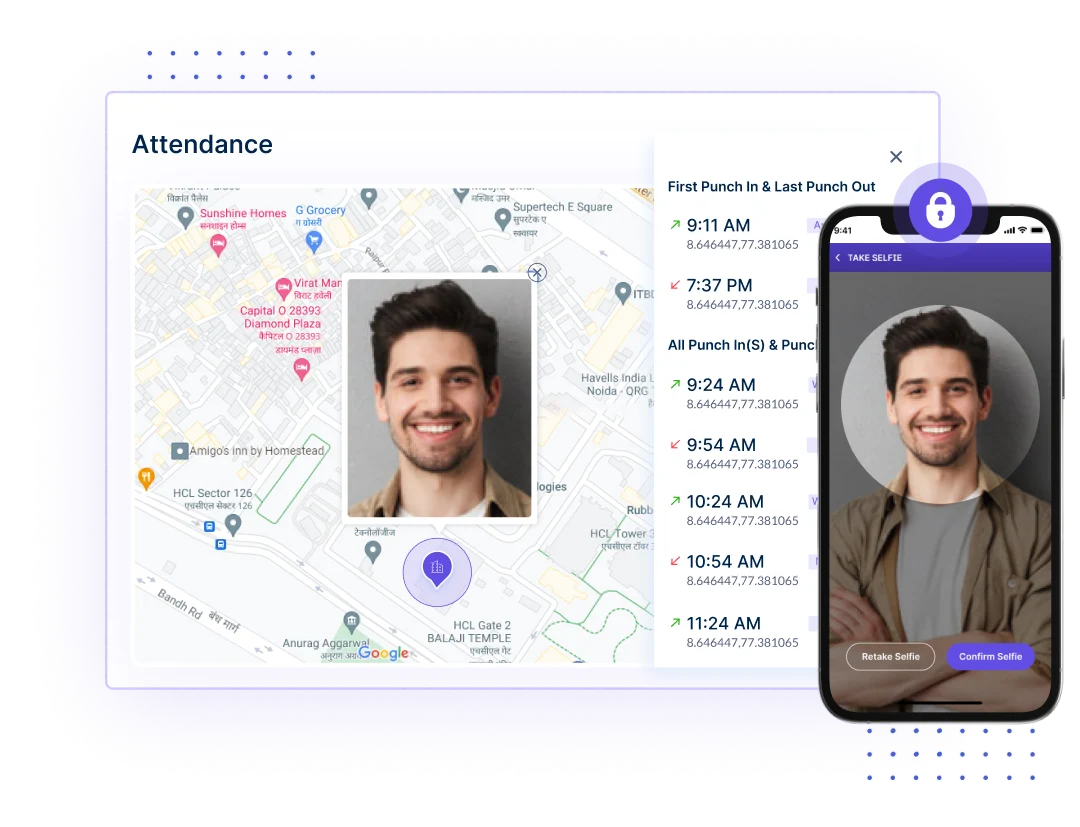
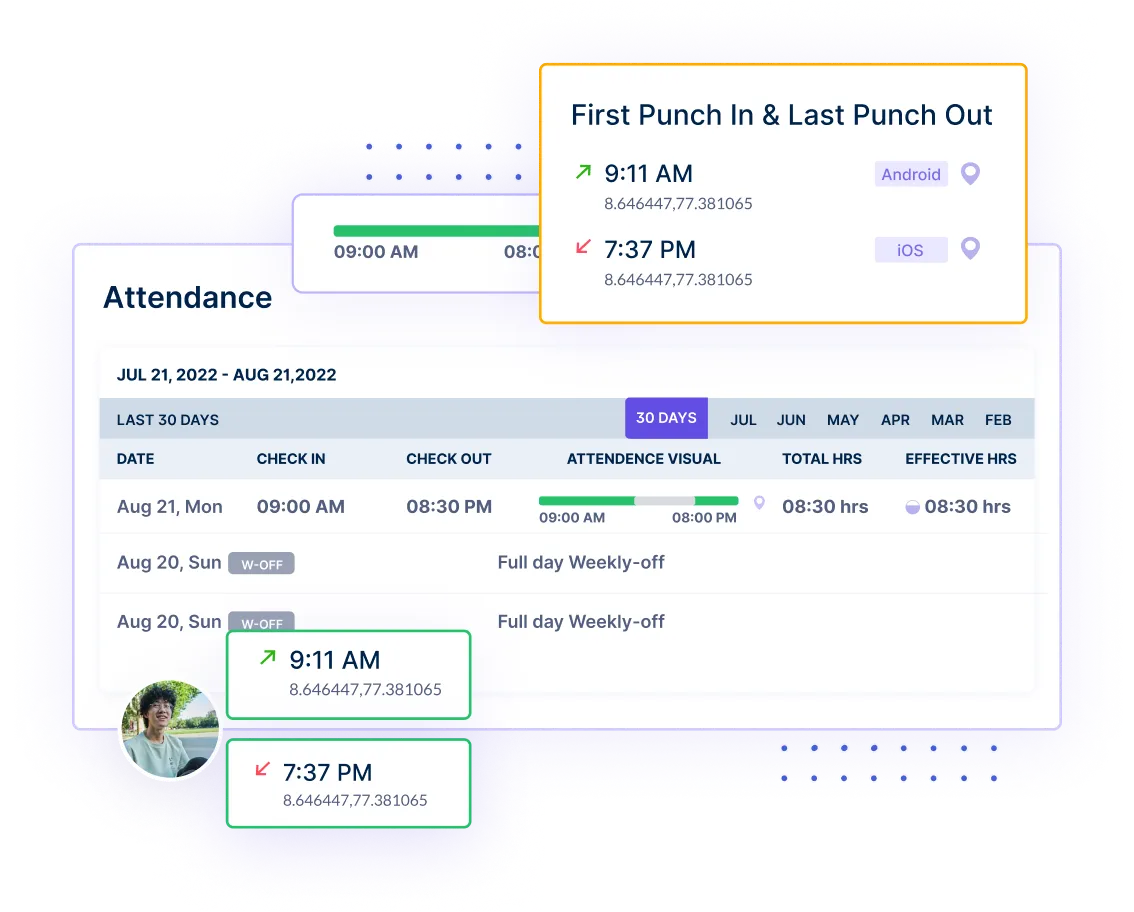
Workstatus Geofence ensures your data is protected within defined geographical boundaries. Receive alerts if sensitive data is accessed outside the designated secure zones.

Workstatus ensures that data is encrypted or decrypted based on the employee’s physical location, adding an extra layer of protection against loss.

With Selfie Validation, ensure biometric integrity for data access. Receive real-time employee verification, preventing unauthorized access and ensuring only authorized personnel can interact with sensitive information.

Elevate your data security with Workstatus Geofence Vigilance. Extend protection beyond physical boundaries, ensuring a robust shield for sensitive information.
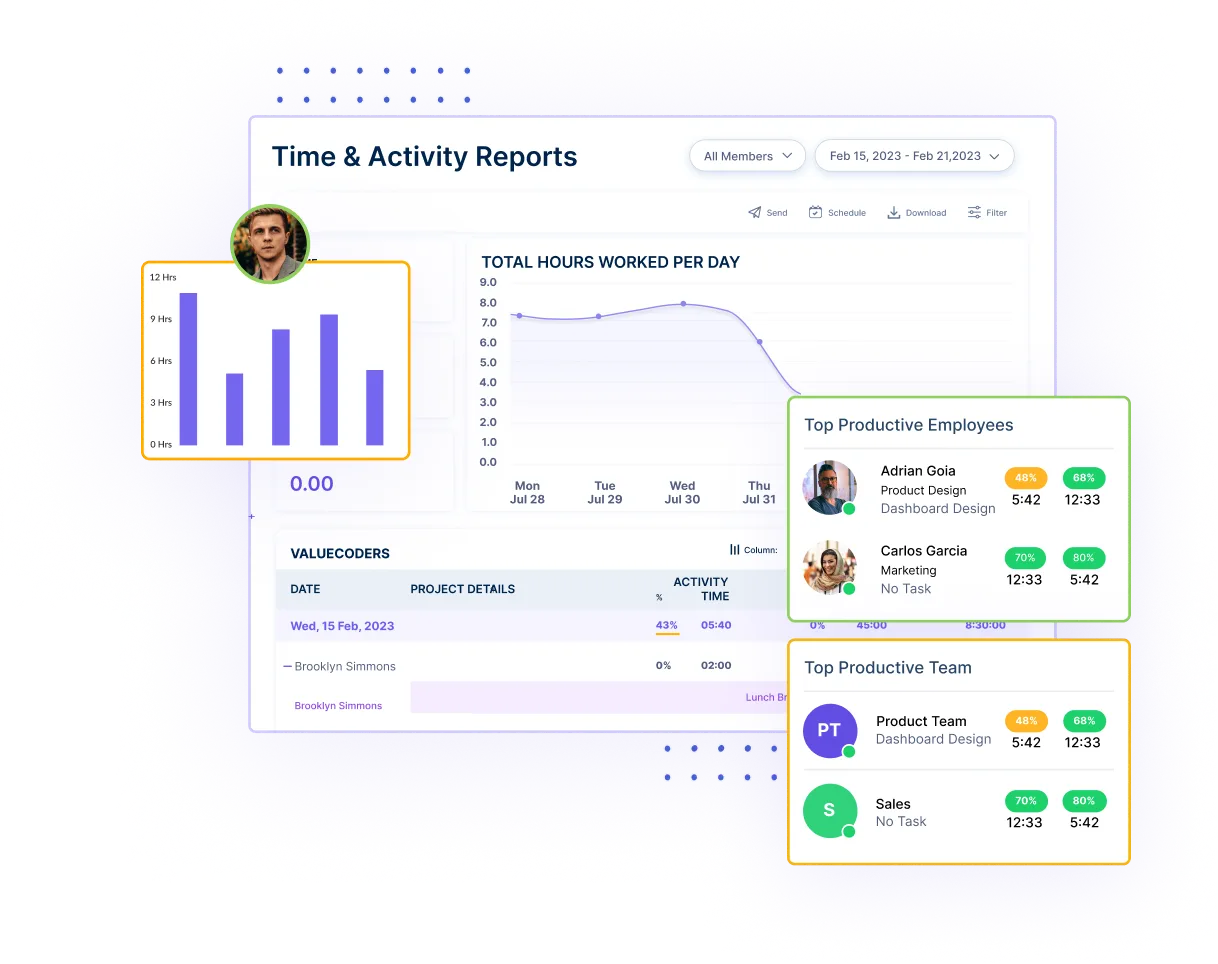
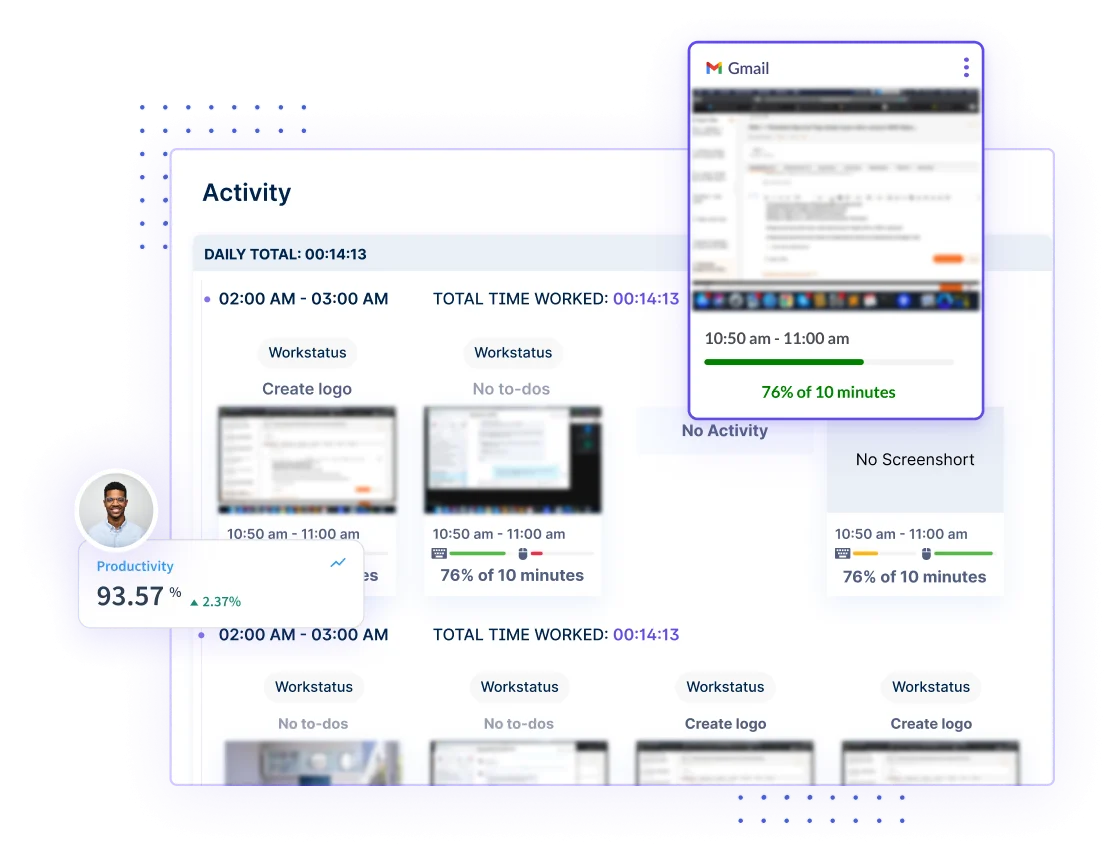
Leverage the power of Employee Monitoring to track data interactions in real time. Identify potential threats by monitoring employee activities and securing your data from internal vulnerabilities.

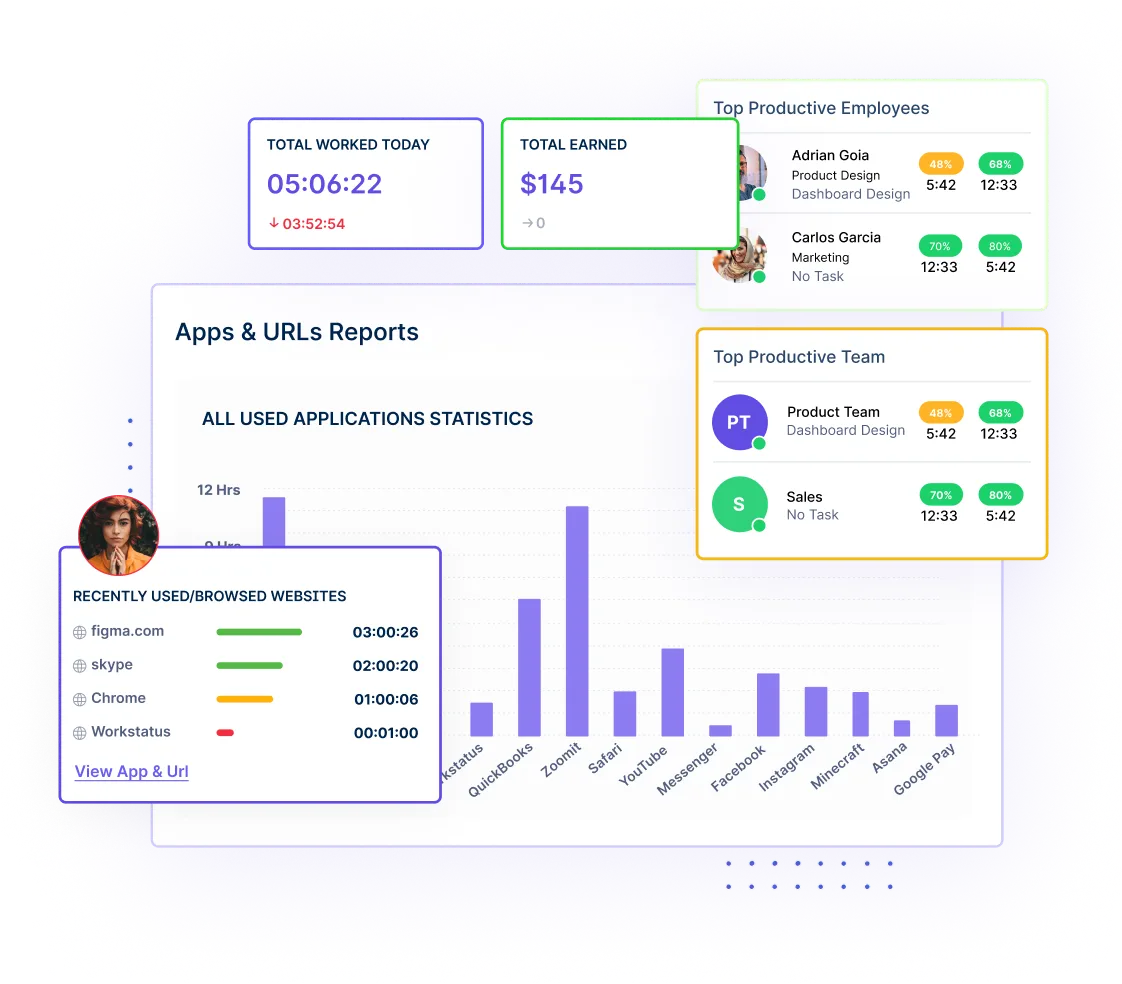
Gain granular control over data access by monitoring Application and Website Usage. Workstatus provides real-time insights into employee interactions, ensuring the secure handling of sensitive information.

Elevate your security with Screenshot Authentication. Automatically capture and validate employee actions to prevent unauthorized access and potential data breaches.




Safeguard your data with Workstatus, bridging security gaps effectively. Trust Workstatus to fortify your digital assets and maintain a resilient defense against potential threats.


Workstatus is equipped with Behavior-Based Alerts. Receive instant notifications when employee activities deviate from the norm, enabling proactive intervention to prevent potential data leaks.

Extend your data protection beyond the office. Monitor and control data access with Workstatus Mobile Application Surveillance, ensuring secure interactions even when your team is on the go.

Workstatus seamlessly integrates with various third-party applications, ensuring a unified security ecosystem. Safeguard your data across platforms without disrupting your workflow.

Workstatus empowers managers across various departments, providing robust features to secure your data.


Features for transparent data protection
Monitor data interactions in real-time to prevent potential breaches.
Monitor and control application and website usage to prevent unauthorized access.
Ensure secure data access through real-time identity validation.
Leverage predictive analytics to anticipate and address potential data threats.
Monitor screens without interfering with employee workflows for seamless operations.

All team members effortlessly download the Workstatus app on their devices (Windows, Mac, Android, iOS) to kickstart robust data loss prevention measures.
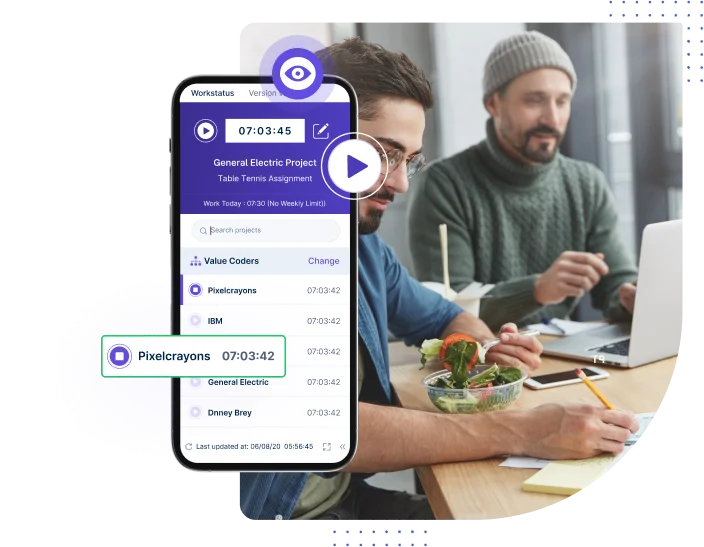
A single click launches the tracker, initiating seamless employee monitoring. Let our automated screen monitoring app monitor your time, tasks, and activities, ensuring a secure monitoring experience.
Team leaders gain access to automated reports detailing time, productivity, and other critical monitoring metrics. Utilize this valuable information to enhance team efficiency while ensuring robust data loss prevention measures are in place.
Transforming Workforce Productivity and Project Excellence

Login as employee or manager and start customizing reports in your respective dashboards based on relevant time tracking done.

Get access to APIs and integrate Workstatus data with any other tool/software your team is using for a single user interface.

Use raw data to generate custom reports on the minutest details on second-by-second tracking of your team’s time.

Get real-time visibility into how developers spend their time. Managers can identify inefficiencies, optimize workflows, and improve productivity.

Empower your organization with advanced tools to detect and prevent fraudulent activities through User Activity Monitoring (UAM).

Safeguard your sensitive data, empower remote collaboration, and ensure compliance with industry regulations.
Our lightweight app allows you and your team to track time, no matter where you are. With GPS tracking and geofencing, anyone can clock in automatically when they enter a job site or get reminders based on location.
Workstatus account required to use apps
Data loss prevention (DLP) is like having a guard for your company’s important files. It stops sensitive information from leaving your business by accident or getting stolen.
When people work from home, keeping company data safe gets much harder. Remote employees use their own computers, home internet, and work from public places.
Why DLP matters for remote teams:
Data protection software like Workstatus helps companies keep their information safe no matter where people work.
How it protects your business:
The right tools will help you keep company data safe, no matter where your team works from.
Companies need to watch what their employees do online to catch dangerous actions before they cause problems.
Many data thefts happen because people visit bad websites or use risky apps that let hackers in.
Monitoring software tracks which websites teams visit and what apps they use during work time.
Risky things to watch for:
How watching helps stop data theft:
Building trust with employees:
The goal of data loss prevention software is to protect your business from costly mistakes, not to monitor employees. It’s about creating a safer digital environment for everyone.
Automated screenshots work like a security feature for computer screens. They take pictures of what teams see on their computers during the day.
Cloud-based DLP software like Workstatus can take screenshots by itself without making computers slow or stopping work.
These screenshots create a record of who looked at what information and when.
How screenshots protect secret data:
Real-time workforce tracking through screenshots helps managers spot problems as they happen.
Benefits of instant monitoring:
Protecting good employees:
Balancing security and privacy:
Tracking what workers do on their computers helps companies spot warning signs before data gets stolen or leaked.
Most security problems start with small weird behaviors that turn into big thefts.
Data loss prevention software for businesses tracks patterns that might mean trouble.
What the software monitors:
Warning signs that activity tracking catches:
Automated activity monitoring with Workstatus works all day to identify these red flags.
How automated systems help:
Quick response to threats:
The goal is creating a safety net that prevents insider threats before they wrongly impact the business.
Building strong data protection needs multiple layers working together like a complete security system.
No single tool can stop all data threats, so companies need several parts protecting their information.
Finding and Labeling Data:
Access Controls:
Identifying and Finding Problems:
Rule Enforcement:
Worker Training:
Smart Automation Features:
Problem Response Planning:
Putting all these pieces together creates a strong system that keeps your company’s data safe at every step.
Usage reports and activity logs work like detailed receipts for everything that happens with company data. They create permanent records that prove businesses follow legal rules and company policies.
Many industries have strict laws about protecting customer information, money records, and personal data.
Why detailed records matter:
How reports help follow rules:
Data protection software for compliance automatically makes these reports without extra work from workers.
Benefits of automated reporting:
Benefits for company audits:
Protection from false claims:
Staying ahead of requirements:
This kind of transparent, always-on reporting builds confidence, keeps your business audit-ready, and proves your dedication to data protection.
We take your data security seriously. Workstatus implements advanced encryption protocols and follows stringent compliance guidelines to protect your information.

SOC 2 Type II attestation is our commitment to the highest standards of data security, privacy, availability, processing integrity & confidentiality.

Fully compliant with the General Data Protection Regulation (GDPR), we adhere to strict guidelines regarding the collection, storage, and processing of personal data.

Our ISO 27001 certification signifies adherence to international standards for information security management systems (ISMS).

We are dedicated to upholding the stringent requirements of the Health Insurance Portability and Accountability Act (HIPAA).
Workstatus strengthens your remote team’s security by providing full visibility into their digital activity.
With Workstatus, your distributed workforce remains productive while reducing the risk of data exposure.
Yes, Workstatus offers proactive monitoring that helps you respond before a security incident turns into data loss.
By staying ahead of suspicious activity, Workstatus helps you stop breaches before they escalate.
Workstatus combines productivity tracking with built-in data protection tools for a complete solution.
With Workstatus, you get more than DLP, you gain control over how and where work happens.
Workstatus gives you granular control over who can access what data, and when.
With these controls, Workstatus helps enforce boundaries and reduce insider risks.
Workstatus is designed to help businesses maintain compliance while keeping operations efficient.
Workstatus gives you the tools to stay compliant without slowing down your team.
Track time and productivity effortlessly.
Customized Solutions for Maximum Productivity