Experience the Power of Productivity
Make your team 40% more efficient. Set up your account in just 2 minutes!
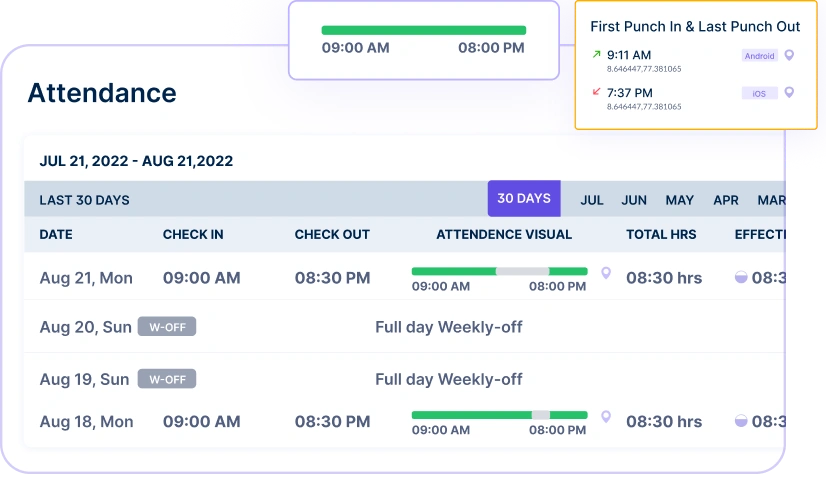
Easily check work hours, reduce time theft, and ensure accurate attendance records—all in one place.
Track work hours, manage attendance, and monitor team activity on-the-go, all from your mobile device.
Active users
Hours Tracked
Monitor your workforce with instant visibility into attendance data, helping you make quick and informed decisions about staff deployment.
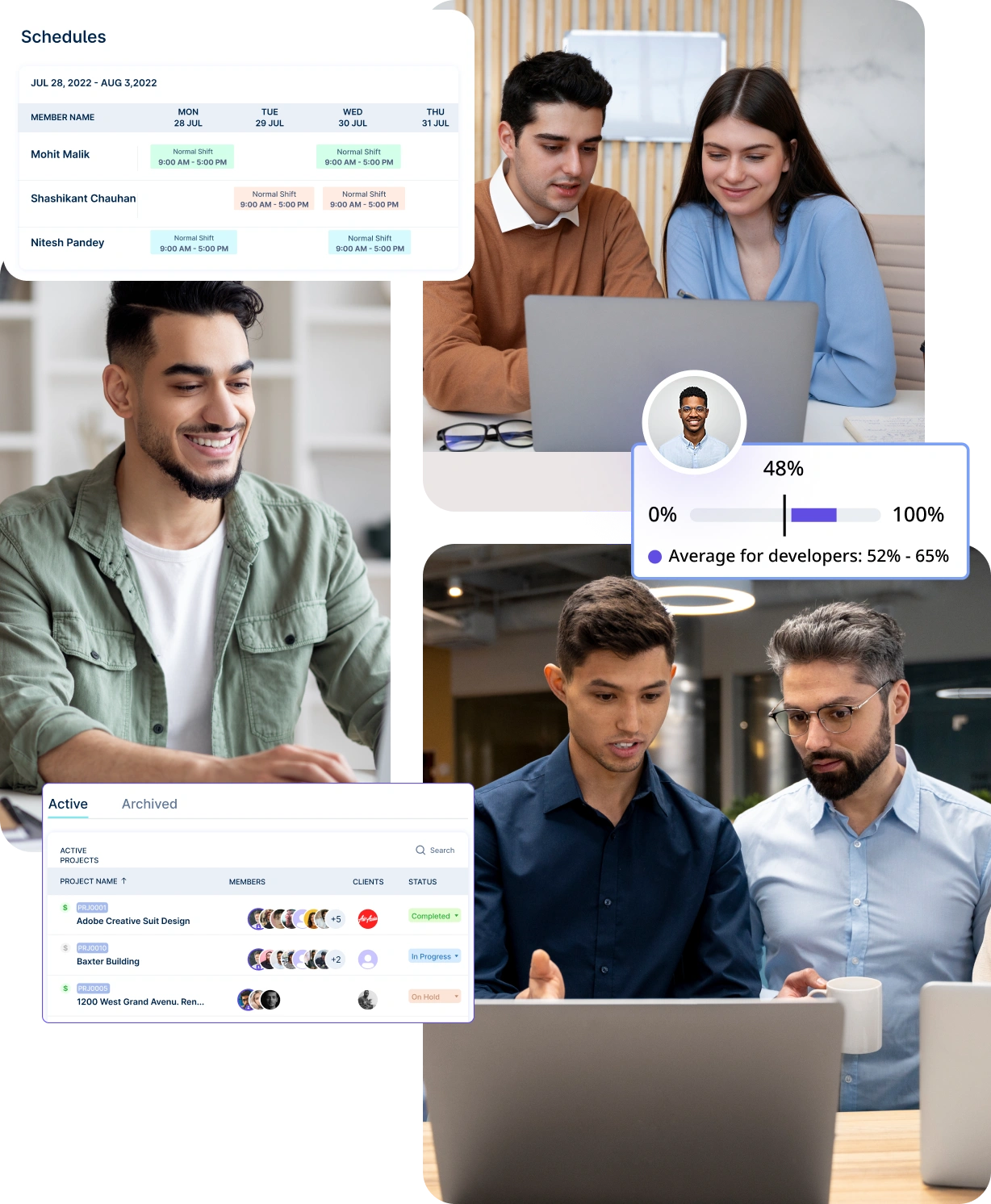
Track live attendance data for immediate oversight of onsite teams and performance across multiple locations and shifts.
View current attendance status to confirm employee presence at work locations effectively and manage workforce distribution seamlessly.
Eliminate buddy punching and false check-ins through face recognition attendance system, ensuring authentic attendance records across all locations.
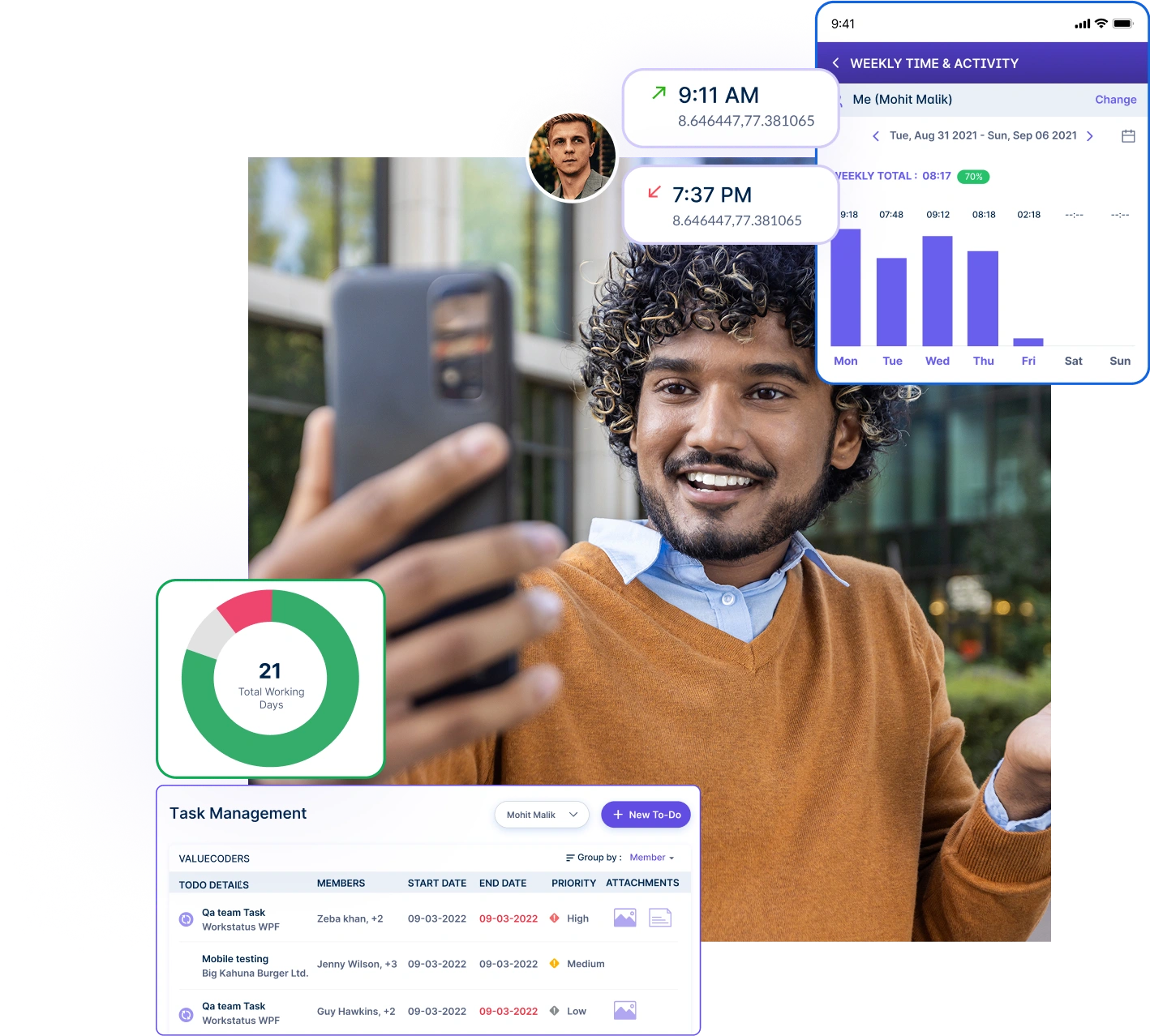
Prevent time fraud with selfie check-ins and GPS tracking capabilities while ensuring authentic attendance verification at all times.
Ensure precise compensation based on actual hours worked and attendance, promoting transparency and accurate payroll processing.


A multi-national marketing firm, boosted overall efficiency.
Increase Your Team Productivity
A Delhi-based startup achieved 30%+ increased ROI with Workstatus.
Enhance Your Business ROIGenerate comprehensive attendance reports to identify trends, optimize scheduling, and improve workforce management with data-driven insights.
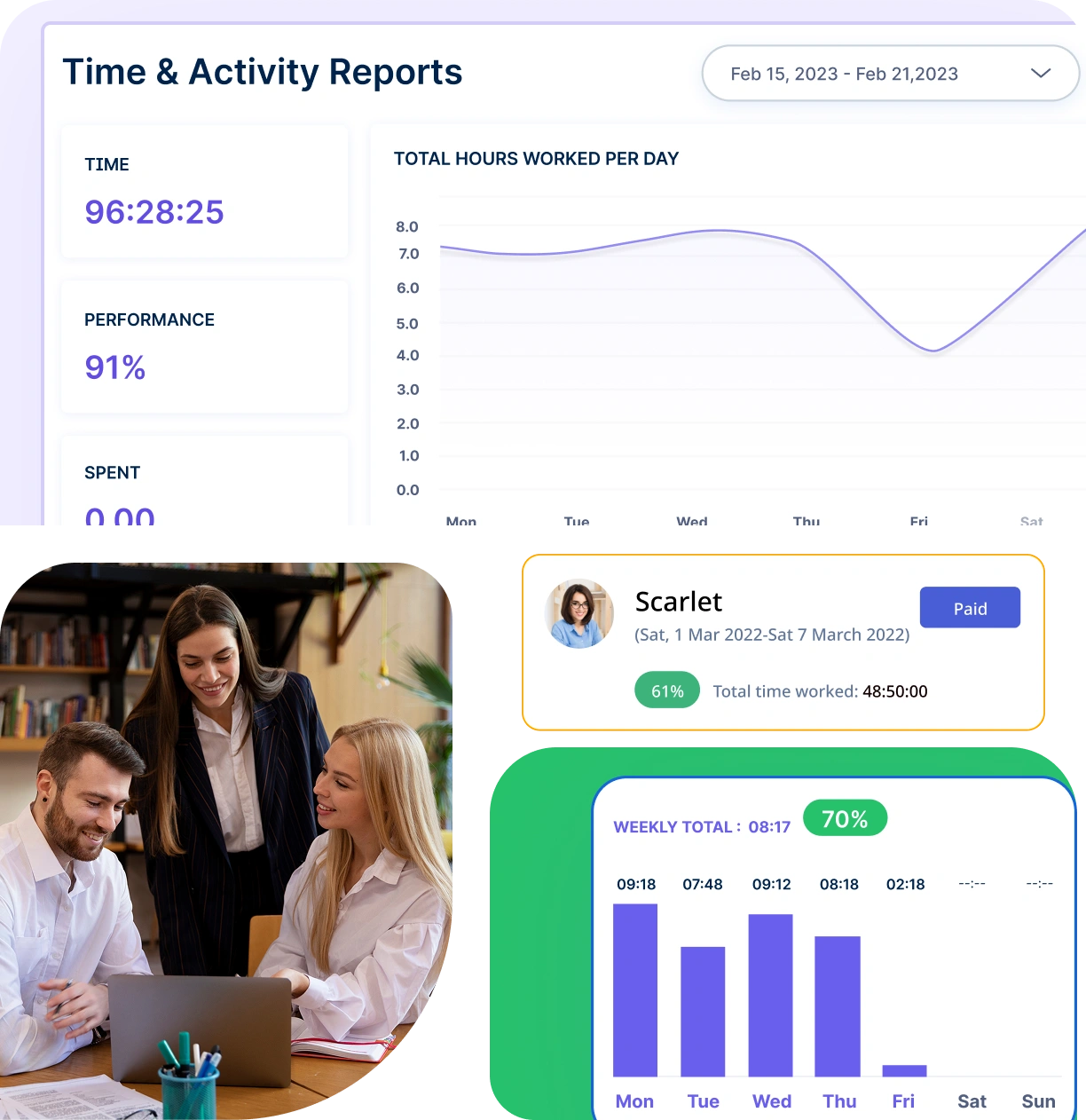
Tailor reports to specific needs, allowing you to focus on particular periods, departments, or projects for more relevant insights.
Accurate reports provide comprehensive attendance data, allowing you to analyze patterns and make informed decisions to improve workforce management.
Get clearer visibility, smarter decisions, and stronger workforce performance- powered by automation and intelligence.
Quick setup, smooth move
A unified intelligence layer that connects your people, projects, and operations.
Unlock workforce potential with digital habits, workload signals, and focus trends-without micromanaging.
Real-time visibility into progress, blockers, delivery estimates, and verified balance for every project.
Clear visibility into billable hours and invoice-ready time, ensuring accurate billing and healthier margins.
Cross-team insights into capacity, utilization, and performance health across roles, teams, and departments.
GPS & geofenced check-ins, biometric verification, shift scheduling, payroll, and compliance-all in one place.
Work together effortlessly, no matter where your team is located, with tools that keep communication and collaboration smooth.

Stay connected and accountable

Balance productivity everywhere

Empower field team efficiency

Optimize office productivity
From IT to healthcare, retail to manufacturing, Workstatus adapts to meet your industry’s unique needs.


We provide clarity, no matter the industry, by showing you:
Analyze and assess tools side by side to choose the best fit for your team’s needs and goals.
From time tracking to advanced analytics, Workstatus has everything your business needs to elevate operations.
Workstatus fits seamlessly into your existing tools, connecting time, tasks, and insights without changing how your teams work.
Managing employee attendance is a tricky task that many companies face today.
The main challenges in tracking employee attendance include:
While these challenges exist, using modern attendance tracking tools and clear policies can help companies manage their workforce better.
With different work setups becoming common, organizations need smart ways to keep everyone following the rules.
Here are the key ways to ensure compliance:
By using the right tools and creating clear rules, organizations can make sure everyone follows policies, no matter how or where they work.
Real-time data has changed the way companies track their employees’ attendance, making everything faster and more accurate.
Here are the main benefits of using real-time data:
Real-time data not only makes attendance tracking easier but also helps companies make better decisions about their workforce every day.
Time theft and buddy punching are serious problems that cost businesses money, but there are effective ways to prevent them.
Here are the key methods to stop these issues:
By combining the right technology with clear policies, businesses can greatly reduce time theft and create a fairer workplace for everyone.
Understanding attendance patterns helps companies make smarter decisions about scheduling their employees.
Here are the key ways attendance insights improve scheduling:
When companies use attendance insights wisely, they can create schedules that work better for both the business and its employees.
Flexible attendance policies are becoming more important as companies mix office and remote work.
Here are the main benefits of flexible attendance policies:
Flexible attendance policies, when backed by the right technology, create happier teams and better results for everyone.
Workstatus automates attendance tracking to ensure accuracy and efficiency. With features like:
This eliminates manual errors and helps businesses maintain precise attendance records
Yes, Workstatus is designed for all work environments, including remote and hybrid setups. It provides:
With Workstatus, businesses can track attendance seamlessly, regardless of location.
Workstatus ensures accurate and tamper-proof attendance tracking through:
These features reduce time theft and ensure fair attendance reporting.
Yes, Workstatus generates real-time, data-rich attendance reports that provide insights into:
As a leading attendance management software, Workstatus helps businesses stay compliant and improve workforce efficiency.
By providing real-time insights into attendance and work patterns, Workstatus helps businesses:
Being the best attendance management software, it simplifies workforce tracking while boosting productivity.
Workstatus the best attendance management software automates attendance tracking through its user-friendly interface, facial recognition technology, and GPS tracking. It also sends notifications to managers and employees and generates accurate reports.
Yes, Workstatus the staff attendance software can track attendance for remote workers through its mobile app and web-based platform. It uses GPS tracking and timestamps to record the start and end of work shifts, and it sends notifications to managers and employees.
Workstatus helps in tracking and managing employee absences through its leave management feature. It allows employees to apply for leave requests, and managers can approve or reject them. It also generates reports on employee attendance and absenteeism.
Workstatus attendance management system can easily integrate with your organization’s existing HR and payroll software through its API.
Yes, Workstatus provides real-time staff attendance software for managers and supervisors. It offers live attendance tracking through its mobile app and web-based platform, and it generates accurate reports on employee attendance and absenteeism.
Managing your workforce, projects, and reports gets simple & effective.
Managing your workforce, projects, and reports gets simple & effective.

Workstatus is highly rated on Trustpilot for reliability, ease of use, and workforce visibility.
Explore MoreGet detailed and clean activity reports of your team.