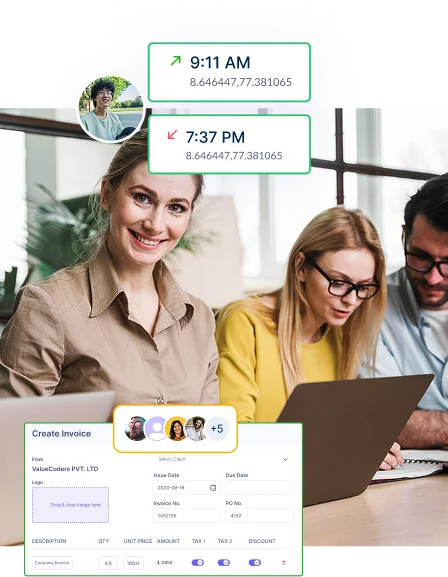
Experience the Power of Productivity
Make your team 40% more efficient. Set up your account in just 2 minutes!
Gain full visibility into employee activity to identify unusual behavior, prevent insider breaches, and secure confidential business information.
Check employee activity, track productivity, and detect potential insider threats in real time to protect your business.
Active users
Hours Tracked
Track work patterns, app usage, and file access to detect anomalies and unauthorized data handling early.

Gain detailed insights into employee activity, idle time, and digital behavior while capturing visual records of work.
Keep a tab on digital footprints to identify risky platforms, unsafe websites or unauthorized tools.
Protect critical information by identifying insider risks and enforcing data security controls across your teams.
Limit and manage access to confidential files based on user roles, permissions, and team responsibilities.
Workstatus adheres to industry-standard certifications like ISO 22301, ISO 27001, SOC 2 Type II, and PCI-DSS.


A multi-national marketing firm, boosted overall efficiency.
Increase Your Team Productivity
A Delhi-based startup achieved 30%+ increased ROI with Workstatus.
Enhance Your Business ROIEnsure your organization stays compliant while protecting employees and sensitive data during online activity.
Generate detailed reports that align with audit, legal, and regulatory requirements to maintain full transparency.
Identify usage of high risk terms in emails, chats, unsafe websites, and documents to prevent data leaks.
Workstatus helps organizations detect insider risks early, protect confidential data, and maintain trust through proactive monitoring and reporting.
Quick setup, smooth move
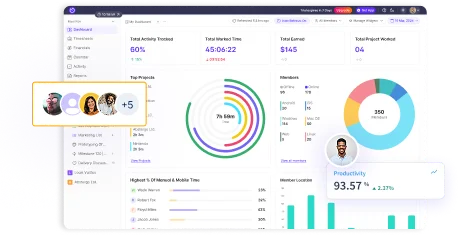
A unified intelligence layer that connects your people, projects, and operations.
Unlock workforce potential with digital habits, workload signals, and focus trends-without micromanaging.
Real-time visibility into progress, blockers, delivery estimates, and verified balance for every project.
Clear visibility into billable hours and invoice-ready time, ensuring accurate billing and healthier margins.
Cross-team insights into capacity, utilization, and performance health across roles, teams, and departments.
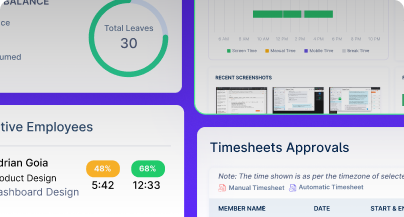
GPS & geofenced check-ins, biometric verification, shift scheduling, payroll, and compliance-all in one place.
Work together effortlessly, no matter where your team is located, with tools that keep communication and collaboration smooth.

Stay connected and accountable

Balance productivity everywhere

Empower field team efficiency

Optimize office productivity
From IT to healthcare, retail to manufacturing, Workstatus adapts to meet your industry’s unique needs.


We provide clarity, no matter the industry, with
Analyze and assess tools side by side to choose the best fit for your team’s needs and goals.
From time tracking to advanced analytics, Workstatus has everything your business needs to elevate operations.
Workstatus fits seamlessly into your existing tools, connecting time, tasks, and insights without changing how your teams work.
Insider threat detection software like Workstatus protects companies from risks that come from their own employees or partners. These threats happen when someone with access misuses company information.
An employee might steal data before leaving. A contractor could share secrets with competitors. Even good employees can accidentally expose private information.
These incidents often go unnoticed until significant damage has already occurred.
One insider incident can destroy years of business relationships and trust. The cost of recovering from insider threats often exceeds the investment in preventing them.
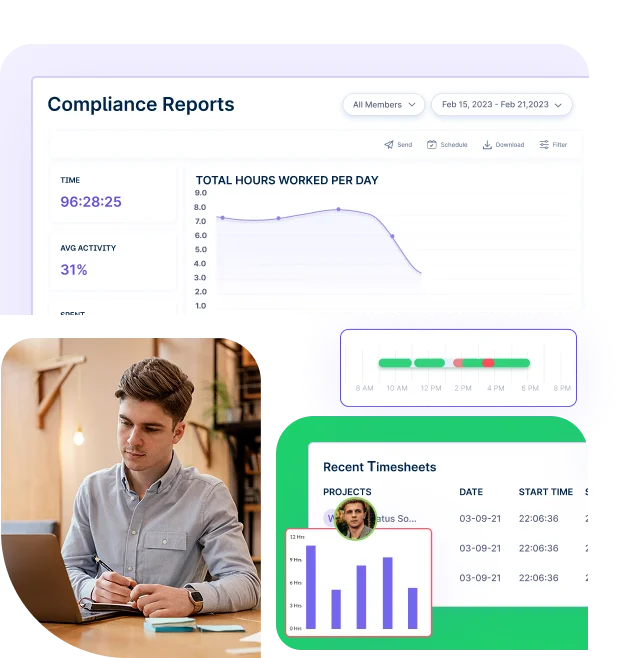
Insider threat detection software tracks how employees use company systems and files.
It notices unusual patterns like accessing files they don’t normally use or download large amounts of data outside business hours.
The system works automatically without requiring constant manual oversight.
This helps security teams focus on real threats instead of reviewing every single action.
The best insider threat detection tool like Workstatus runs quietly and only flags suspicious activity.
Effective insider threat detection techniques start with controlling who can see what information. Not every employee needs access to everything.
These controls reduce risk while allowing employees to do their jobs efficiently. Setting up proper access from the start prevents problems down the road.
Strong controls mean unauthorized people can’t reach sensitive information. Insider threat detection tools work best with these preventive measures.
An insider threat solution like Workstatus checks for warning signs of unusual activity. The system compares current behavior against normal patterns and sends alerts when something looks wrong.
Early detection helps you address issues before they become serious breaches. Security teams can investigate quietly and take action to prevent data loss.
Quick detection through insider threat detection software gives you time to investigate and stop problems.
Insider threat detection software often includes safe browsing features that protect employees from accidentally visiting dangerous websites or downloading harmful files.
These tools monitor internet activity to catch threats before they can damage company systems.
Safe browsing blocks access to known malicious websites and phishing pages. It also scans downloads in real-time to stop malware from entering the network.
The best insider threat detection tool like Workstatus combines safe browsing with activity monitoring for complete protection.
This dual approach stops both external attacks and internal misuse of company resources.
Clear internet usage policies help employees understand what’s acceptable and keep company data safe.
These policies work alongside insider threat detection tools to create a secure browsing environment.
Written guidelines remove confusion about what employees can and cannot do online.
Regular training ensures everyone stays aware of current threats and best practices.
Strong policies combined with insider threat detection techniques create multiple layers of defense.
Employees know the rules while monitoring systems catch violations and external threats automatically.
Companies must balance security monitoring with privacy laws and employee rights when using insider threat detection software.
Clear policies help employees understand what to expect and why monitoring exists.
Transparency builds trust while maintaining security standards.
Regular compliance reviews ensure your monitoring practices stay within legal boundaries.
The right approach protects the company while respecting employee rights.
Insider threat detection involves monitoring employee activity to identify potential risks like data theft or unauthorized access. Workstatus provides real-time tracking of user behavior, app usage, and file access to detect such threats early.
While there are several solutions available, Workstatus stands out for its user-friendly interface, comprehensive monitoring capabilities, and seamless integration into existing workflows. It provides a balanced approach to security and productivity, making it a top choice for businesses looking to safeguard against insider threats.
Key features of Workstatus that help detect and mitigate insider threats include:
These tools help businesses identify unusual behavior and prevent potential security risks effectively.
Workstatus generates detailed compliance reports that align with audit and legal requirements, such as ISO 27001 and SOC 2. It also tracks user activity to maintain accountability and support regulatory compliance.
Workstatus monitors file transfers, emails, and high-risk keywords to prevent unauthorized sharing of sensitive information. Automated alerts notify administrators of suspicious activities, enabling prompt action.
Managing your workforce, projects, and reports gets simple & effective.
Managing your workforce, projects, and reports gets simple & effective.

Workstatus is highly rated on Trustpilot for reliability, ease of use, and workforce visibility.
Explore MoreGet detailed and clean activity reports of your team.