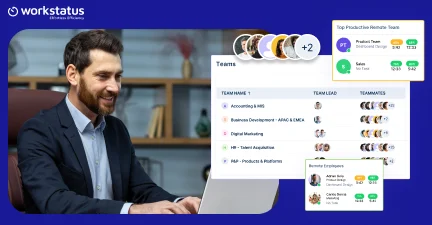
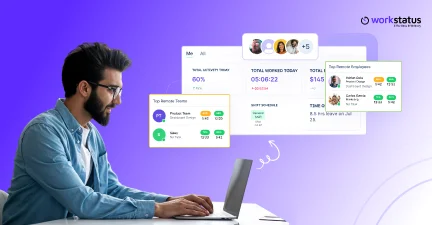
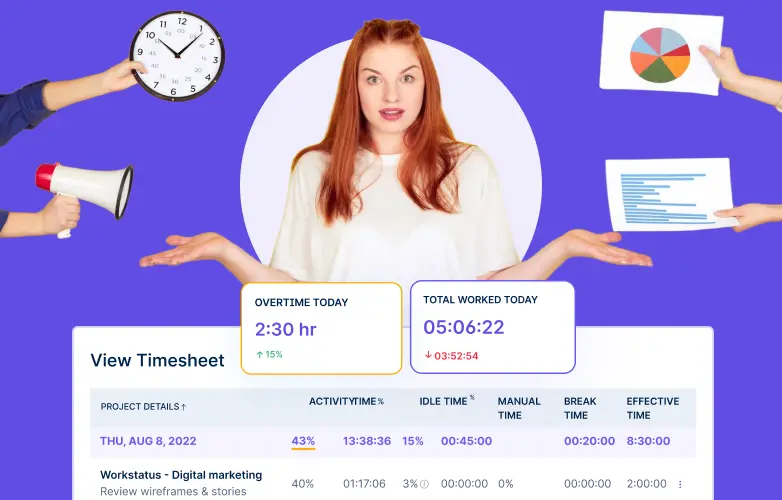
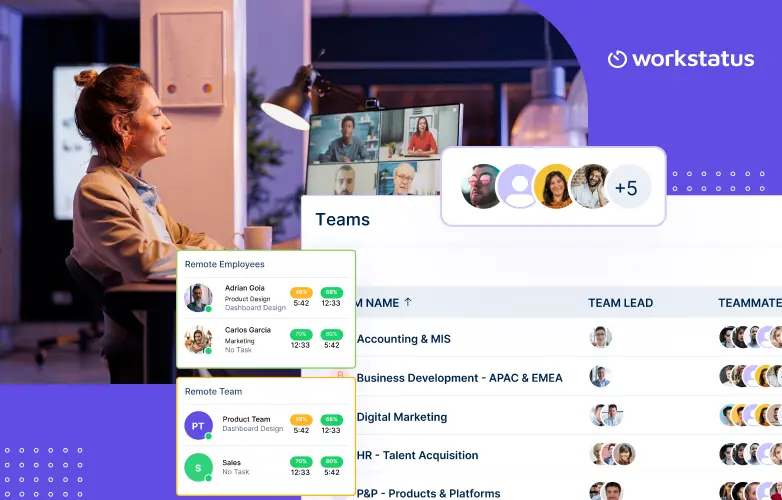
Top 7 User Activity Monitoring Apps for Remote Teams
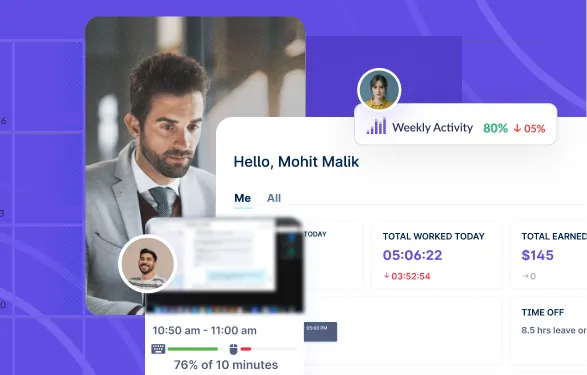
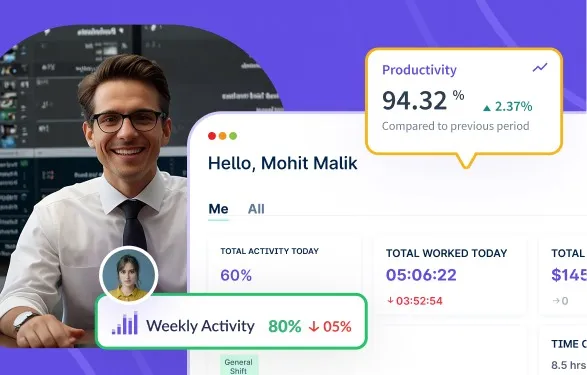
Nearly 78% of employers now use monitoring tools to oversee remote staff. 86% implement real-time tracking of apps and screen...
Nearly 78% of employers now use monitoring tools to oversee remote staff. 86% implement real-time tracking of apps and screen...
A well-established IT company switched to full-time remote work, and things initially looked smooth. However, employees felt disconnected, some left,...
Being a CEO or founder of a business that has mobilized teams worldwide can be challenging without the right tools...
Effective scheduling should align with employee preferences to boost productivity and morale. Flex Time and Comp Time are two popular...
Running a business is not just about hard work, it is about working smart. Without the right systems in place, time, money...
Managing remote teams has grown far beyond communication tools, and with 2025 around the corner, technology continues to play a...
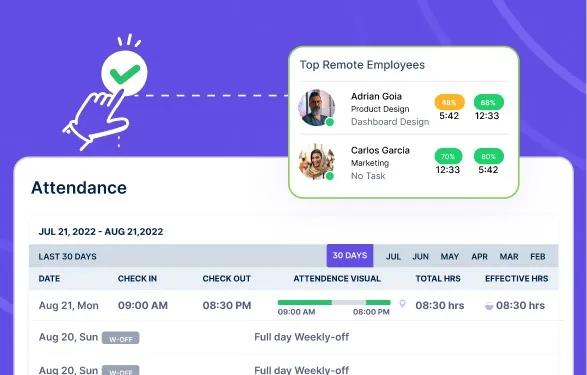
Workforce analytics is not just about counting hours or measuring performance – it provides you with different decisions on how...
Managing remote teams on a budget can feel like herding cats on Zoom while your bank account watches in horror....
The world is going remote, folks. And while it’s finally great to wear sweatpants to work, HR managers are sweating...
Managing schedules, tracking attendance, and handling payroll can be time-consuming and prone to errors. The repetitive cycle of tracking, approving,...
Are you a business owner struggling with monitoring your hybrid and remote workforce? If so, you’re not alone. According to...
Traditional management strategies are ineffective in today’s rapidly changing corporate world. Workforce analytics drives change by transforming conflicting data...