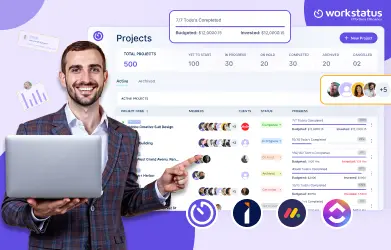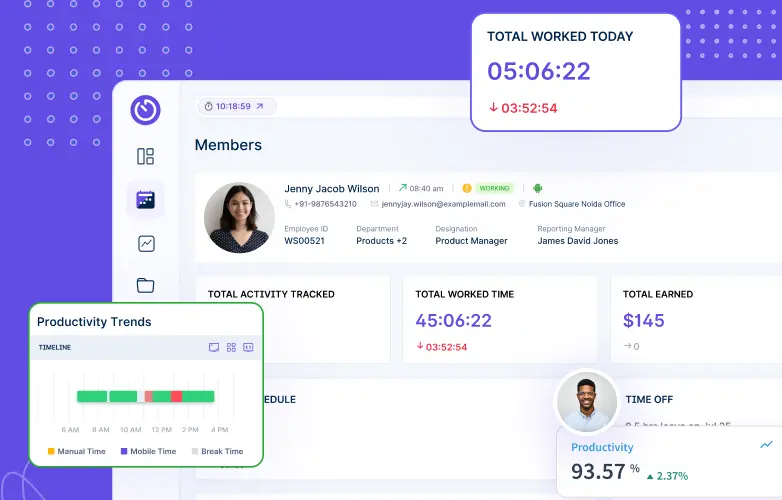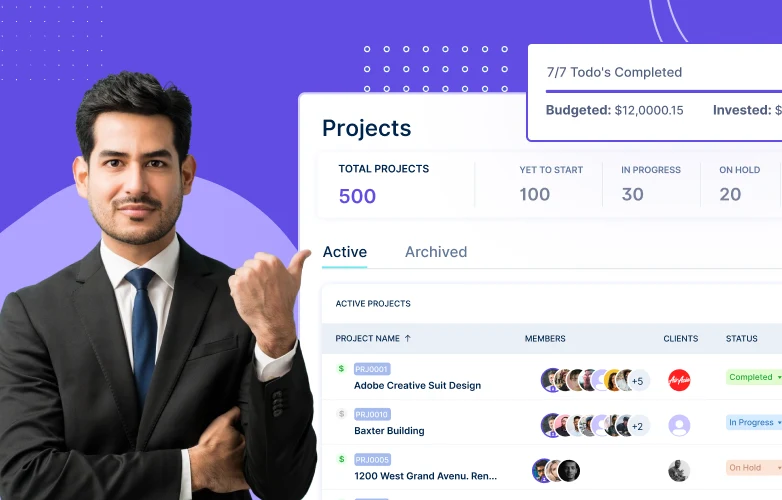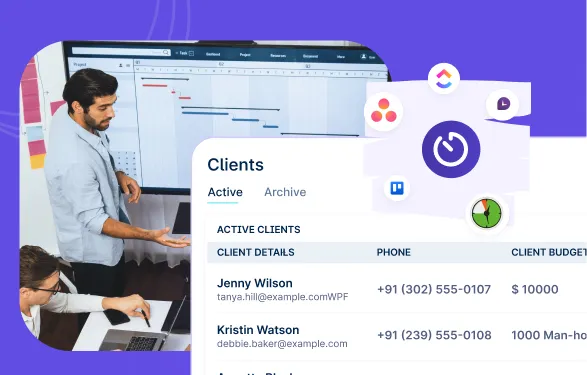
5 Best Project Management Templates for Team Alignment
Project management can sometimes feel like next to impossible. One minute, everything lines up perfectly, and the next, some of...
Project management can sometimes feel like next to impossible. One minute, everything lines up perfectly, and the next, some of...
Just imagine: You’ve got this amazing project lined up with a top-notch team ready to roll and great expectations to...
Let’s face it; as a project manager, you’re likely to have more on your head than a restaurant that has...
Managing tasks without structure is like juggling in the dark—leading to missed deadlines, unclear priorities, and inefficiency. For project managers,...
Managing audits, tax filings, and client requests can be overwhelming—but effective project management changes everything. With the right tools, you...
Balancing tasks in the demanding world of project management is like trying to keep plates spinning on a unicycle –...
Every project manager knows that dealing with the project deadline and group dynamics is quite the norm, only to anticipate...
According to a survey conducted by Gartner, 65% of managers report feeling stressed about their inability to monitor employee productivity...
Collaboration is key for any successful team. However, with competing priorities and busy schedules, it can be hard for...
The rise of remote call centers is a response to the global shifts in work dynamics and also a...
Are you tired of project failures derailing your hard work and investments? Or Ever wondered how some projects seamlessly...
Recently, freelancing has evolved beyond traditional platforms like Upwork, leading to a surge in alternative to Upwork options for...